Cyber security isn’t just about firewalls and fancy software, it’s also about the everyday decisions we make. From clicking a link to choosing a password, our habits and assumptions can quietly open the door to risk. But the good news? With a little awareness and the right tools, those human blind spots can be mitigated.
Let’s explore some of the most common human blind spots in cyber security, and how to stay one step ahead.
Social Engineering
Sometimes, a message looks just right. It might say it’s from your bank, your boss, or your IT team. But it’s not. It’s a trick.
- Phishing: Emails or texts that look legit but are designed to steal info or install malware.
- Impersonation: Attackers pretending to be someone familiar or authoritative to gain access they shouldn’t have. Impersonation isn’t just online. Tailgating is when someone slips into a secure area by following an employee inside the office building, relying on trust and politeness to bypass security.
What helps: Always verify before clicking or responding. Hover over links, double-check sender details, and when in doubt, reach out through a known channel. When it comes to impersonation, if you’re entering your work building, be cautious who may be behind you, don’t scan anybody but yourself in! A friendly smile doesn’t mean they’re supposed to be there.
Password Practices
We all use passwords, right? But if you’re reusing them, choosing ones that are too simple, or leaving them written down somewhere, they’re not really doing much to keep things safe.
Common pitfalls (you’ve probably seen this all before, but it’s still so common!):
- Reusing the same password across multiple accounts
- Writing passwords down on sticky notes or saving them in notes
- Using personal info (like birthdays or pet names) that’s easy to guess
What helps: Use a password manager to generate and store strong, unique passwords. Enable multi-factor authentication (MFA) wherever possible. And consider passkeys, a passwordless login technology based on public-key cryptography. (for more information on password managers and passkeys: NCSC).
Relying too much on tech alone!
Security tools are essential, but they’re not a set-it-and-forget-it solution. Just because you’ve got antivirus software doesn’t mean you’re invincible.
- Assuming cloud services are automatically secure
- Thinking antivirus software is all you need
What helps: Stay involved. Update your software, understand your tools, and don’t rely on tech alone.
Awareness Gaps
Sometimes, it’s just a matter of not knowing what to look for.
- Clicking suspicious links
- Ignoring software updates
- Using public Wi-Fi without protection
What helps: Regular training, staying curious, learn the basics of cybersecurity. Keep a check on your updates, don’t always rely on auto-updates. And please, use a VPN on public Wi-Fi!
Internal Risk
Not all threats come from outside. Sometimes, it’s an employee, either accidentally or intentionally…
- Too much access to sensitive data
- No clear way to report suspicious activity
What helps: Monitor behaviour, limit access (especially to sensitive data that only leadership employees need to see), and create a culture where people feel safe reporting suspicious activity, and make it easy to report concerns.
Shadow IT: The sneaky stuff
It’s tempting to install a new app or use a personal device for work. But if it’s not approved or monitored, it can create security gaps.
- Unapproved software or devices
- Workarounds that bypass IT protocols
What helps: Provide secure, approved tools, and make it easy for teams to request what they need.
Data Sensitivity Missteps
Not all data is equal, but it’s easy to treat it that way.
- Sharing sensitive info over unsecured channels
- Not labelling or handling data properly
What helps: Label data and classification clearly, secure communication tools, and regular reminders about what’s sensitive.
Unclear Incident Response
When something goes wrong, knowing what to do, and doing it quickly, matters.
- Not knowing how to report an issue
- Delays due to confusion or fear
What helps: Clear, simple response plans. Make sure everyone knows how to report something and feels safe doing so!
Here are some quick tips on reducing human blind spots and improving your security hygiene.

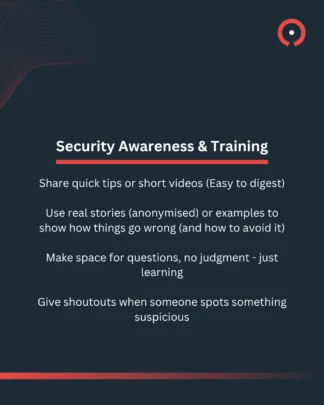
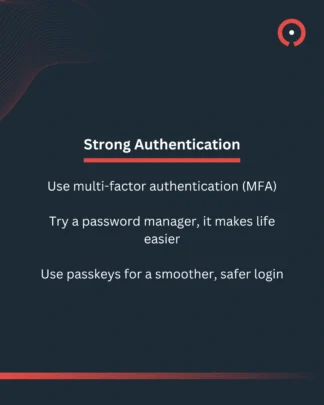
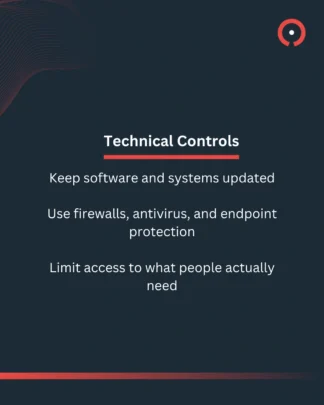
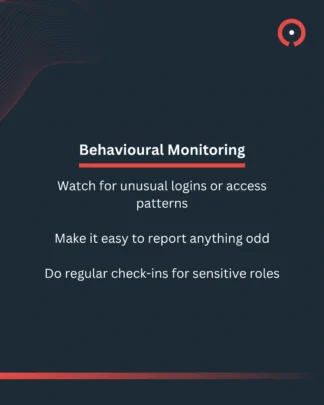


In 2025, Phishing remained the most prevalent type of cyber crime at 93%.
Despite all the tech, it’s the everyday choices, clicking too fast, trusting too easily, skipping training, that open the door.
Whether you’re in a small business or a large organisation, it’s time to stop thinking “it won’t happen to us.”
Because the biggest threat isn’t always the hacker, it could be the human blind spot we didn’t see coming. And the second biggest? Thinking we’ve got no blind spots at all.
InfoSec People is a boutique cyber security and IT recruitment consultancy, built by genuine experts. We were founded with one goal in mind: to inspire people to find the careers that inspire them. With the success of companies fundamentally driven by the quality of their people, acquiring and retaining talent has never been more important. We believe that recruitment, executed effectively, elevates and enables your business to prosper.
We also understand that cyber and information security recruitment can genuinely change people’s lives, that’s why we take the duty of care to those we represent very seriously. All our actions are underpinned by our core values:
- Always do the right thing
- Be the best we can be
- Add value
We work with businesses in the cyber/tech arena, from start-ups and scale-ups to FTSE100 and central Government, many of whom are always looking for great people.
Call us directly on 01242 507100 to discuss opportunities or email info@infosecpeople.co.uk.